When large telecoms, utilities, and even the government are getting hit with data breaches, what chance do you stand? A surprisingly good chance if you take a few key measures. One of those measures is encrypting your hard drive or SSD.

Windows 10 has a way to encrypt your built-in drive with Microsoft’s BitLocker technology. It’s easy to implement, easy to use, and doesn’t require any special skills or hardware. However, you do need to have Windows Pro, Enterprise, or Education versions of Windows 10. If you have Windows 10 Home, VeraCrypt encryption is an excellent option. You may even prefer it to BitLocker.
Contents
What Is BitLocker?
Encryption is the process of changing information into something meaningless unless you have the key. BitLocker encrypts information on hard drives so that it can only be read once the key is entered. The key may be managed by a Trusted Platform Module (TPM) chip in the computer, a USB drive that stores the key, or even just a password. If you try BitLocker and don’t like it, it’s easy to turn BitLocker off.
Why Should I Encrypt My Windows Hard Drive?
Let’s assume you use password best practices. Your password is complex, hard to guess, and you don’t write it down or share it with anyone. If someone wants to get data from your drive and they don’t have your Windows password, they could remove the hard drive, plug it into another computer, and use a Linux live CD to recover files.

If you’re using BitLocker, they can’t do that. BitLocker has to be able to get the key from somewhere. Ideally, that would be the Trusted Platform Module (TPM). It could also be a passphrase or a USB drive dedicated as a BitLocker key.
“But no one is going to steal my drive,” you respond. Have you ever thrown a computer out? Your hard drives went with it too, didn’t they? Unless you safely dispose of a hard drive, someone can get the data. This happens every day, and it’s easy. We even have an article on how to access files on old drives.
If you used BitLocker and took the drive out of the computer then disposed of the computer and drive separately, you just made the casual data thief’s job exponentially harder. It would require a data recovery specialist to even have a remote chance of getting your data. Convinced yet?
How to Check if a Computer Has a TPM
The ideal BitLocker situation is on a device with a TPM. Does your device have a TPM? It’s easy to check.
- Select the Start menu and type system. The first result should be System Information. Select that.
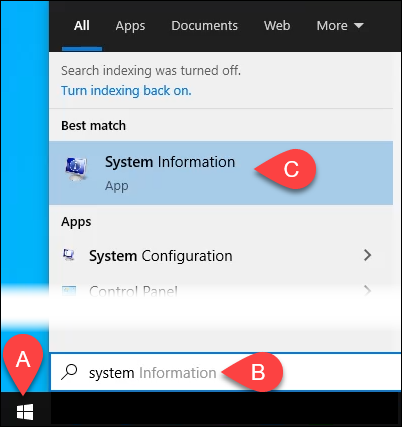
- When the System Information window opens, enter trusted in the Find what: box at the bottom, then select Find or press Enter.
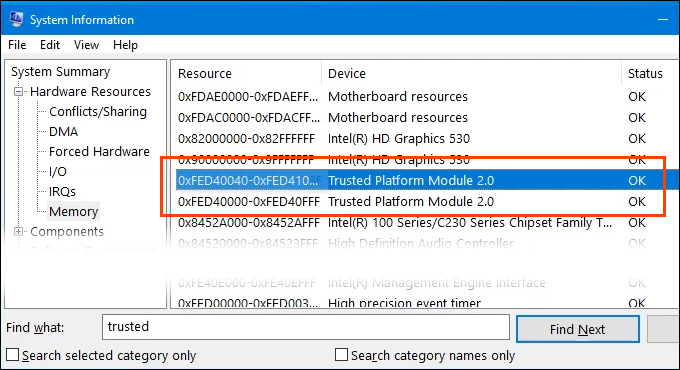
- If the device has a TPM, it will show in the results. In this example, TPM does exist and it’s a version 2.0 TPM. Version may be important in the future, especially once Windows 11 is publicly available.
How to Enable BitLocker On a Device With a TPM
Your device has a TPM, so this next part is simple and easy.
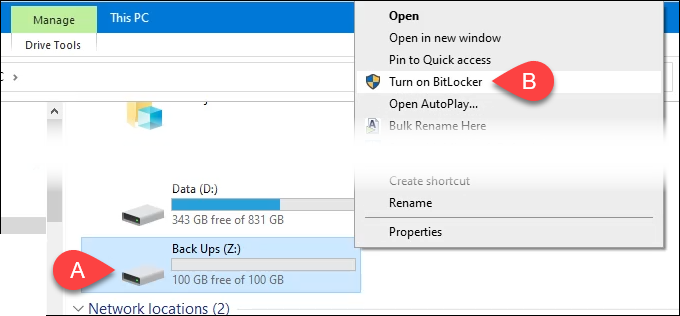
- Open File Explorer and navigate to the drive to be encrypted with BitLocker.
Right-click on the drive and select Turn on BitLocker.
There may be a Starting BitLocker message with a progress bar. Let it finish.
- It will prompt you to Choose how you want to unlock this drive. There are 2 choices; Use a password to unlock the drive, or Use my smart card to unlock the drive. If the device is being used in a business, you may have a smart card and want to use that. If not, then choose to use a password. Create a strong, secure password.
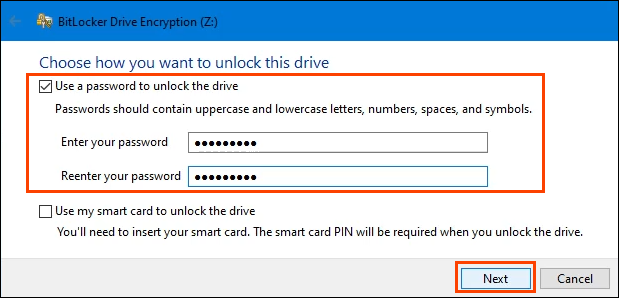
The password will only be needed if the drive is removed from this device and installed on another device. Otherwise, the TPM will handle the entering of the password, making the encrypted drive work seamlessly with everything else.
Now it asks How do you want to back up your recovery key?
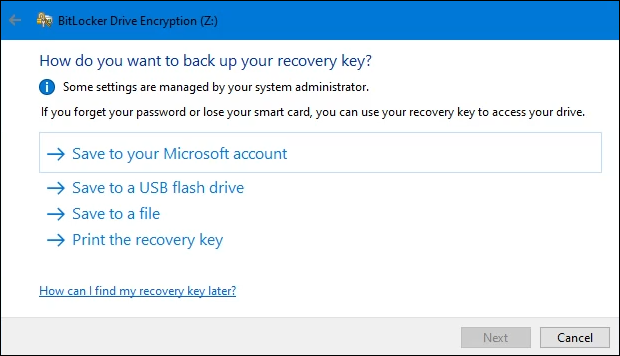
There are 4 options:
- Save to your Microsoft account: If you use a Microsoft account to log in to the device, this is the easiest method. It’s what’s being used in this example.
- Save to a USB flash drive: If this method is chosen, only use the USB flash drive for this purpose. Do not try to store other things on that flash drive.
- Save to a file: If choosing this method, don’t save the file to the drive being encrypted. Save it to another drive or cloud storage.
- Print the recovery key: Choosing this method means the printed key needs secure storage, safe from fire, theft, and flood. When the key is needed, it’ll need to be manually typed in.
Depending on the method selected, there may be some additional steps, but all methods will eventually lead to the next screen.
This step asks to Choose how much of your drive to encrypt. That may be confusing. If there’s nothing on the drive being encrypted, select Encrypt used disk space only. It’s very fast.
Anything added to the drive after this will be automatically encrypted. If the drive already has files and folders on it, choose Encrypt entire drive to ensure they’re all encrypted immediately. Then select Next.
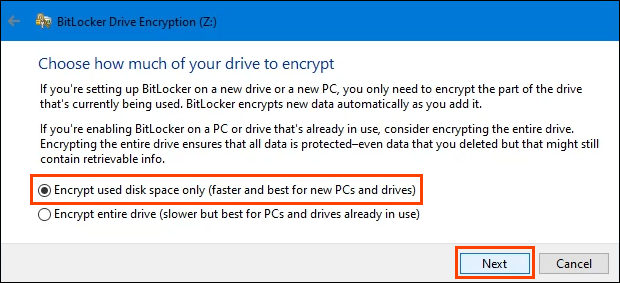
The next screen might not display depending on the version of Windows you’re using. It’s important to take the time to read and understand it.
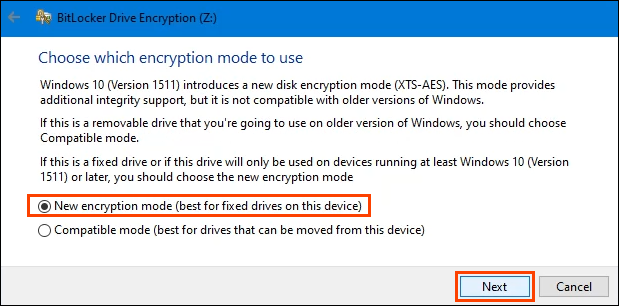
To sum up, if anyone ever takes the drive out of this device and puts it into any version of Windows prior to Windows 10 Version 1511, the drive won’t work. Most people won’t ever do that, so most will choose New encryption mode, then select Next.
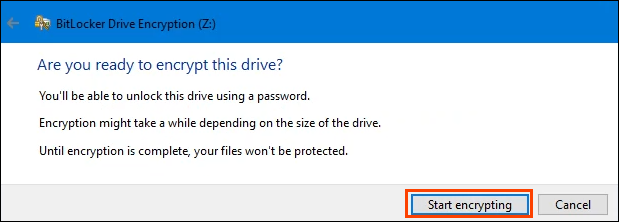
Encryption is serious business and things can go wrong. That’s why the process will ask one last time, Are you ready to encrypt this drive? If so, select Start encrypting.
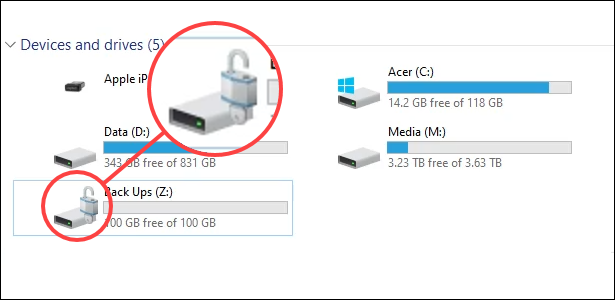
Once BitLocker is done encrypting the drive, go back to File Explorer. Notice that the drive icon now has an unlocked padlock. That means the drive is encrypted but ready to receive files. If the padlock was locked, you would need to enter the password to access it.
How to Enable BitLocker On a Device Without TPM
For now, there is a way to use BitLocker to encrypt a drive even if the device doesn’t have TPM. Expect that to change in Windows 11 as Windows 11 requires TPM 2.0 to upgrade from Windows 10 to Windows 11. This method requires having administrator rights.
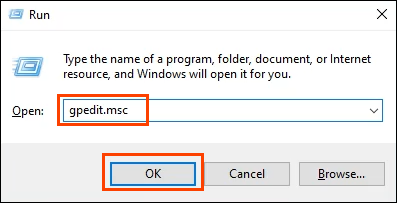
- Press the key combo Win Key + R to open the Run utility. In the Open field enter gpedit.msc, then select OK or press Enter. This will open the Local Group Policy Editor.
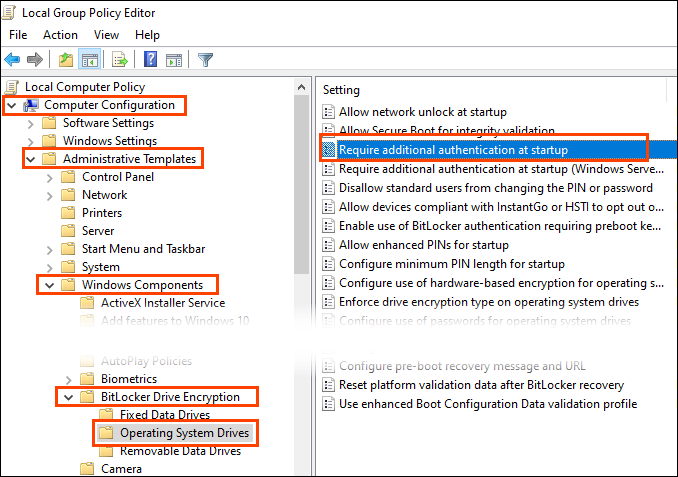
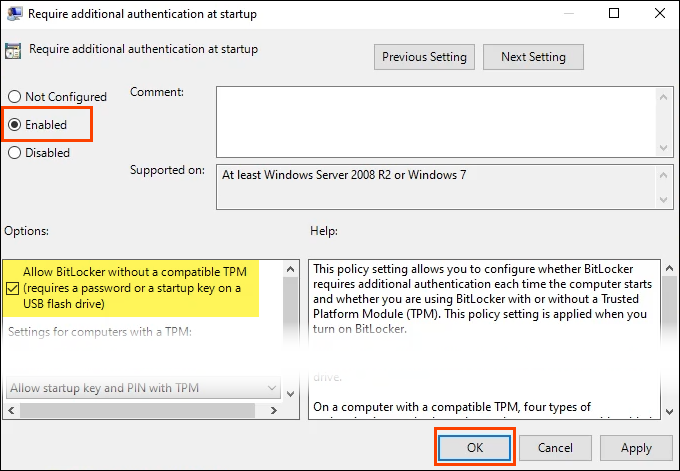
- After the Local Group Policy Editor opens, navigate to Computer Configuration > Administrative Templates > Windows Components > BitLocker Drive Encryption > Operating System Drives. Double-click on the setting Require additional authentication at startup.
- Select Enabled and then OK to change the setting. Note the checkbox where it reads, “Allow BitLocker without a compatible TPM.” This allows for the use of a password or security key to be used to access the BitLocker encrypted drive. Restart Windows to activate the setting.
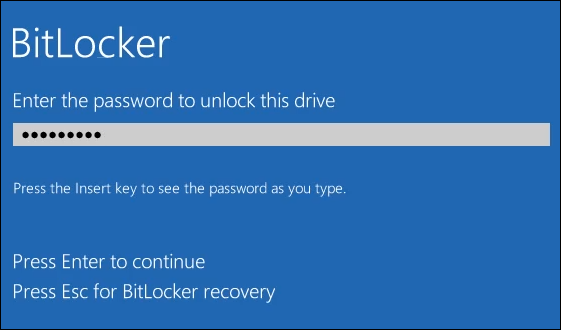
- Follow the same procedure as in the section above to start BitLocker and encrypt a drive. WARNING: If encrypting the Windows drive is done, every time Windows starts, the password must be entered for Windows to load. Record the password in a secure place off of the device.
- The next time Windows is started, BitLocker will require the password to be entered to unlock the drive. Do that and press Enter to continue.
Are You Secure Now?
BitLocker encryption is only one part of securing your data. What else are you doing to ensure your privacy and identity are protected? Let us know! Make sure to check out all of our data security and privacy articles.